Supervisory Control and Data Acquisition (SCADA) systems are used for monitoring industrial devices. However, their security faces the threat of being compromised due to the increasing use of open access networks. The primary objective of this survey paper is to provide a comparative study of the on-going security research in SCADA systems. The paper provides a classification of attacks based on security requirements and network protocol layers. To secure the communication between nodes of SCADA networks, various security standards have been developed by different organizations. We conduct a study of the security standards developed for SCADA networks along with their vulnerabilities. Researchers have proposed various security schemes to overcome the weaknesses of SCADA standards. The paper organizes security schemes based on current standards, detection, and prevention of attacks. It also addresses the future challenges that SCADA networks may face, in particular, from quantum attacks. Furthermore, it outlines directions for further research in the field.
Introduction
SCADA systems are used as control systems for monitoring industrial processes such as oil mining, electric grids, traffic control systems, water treatment plants, space stations and nuclear systems. Modern SCADA systems have been exposed to a range of cyber attacks since they use open access networks to leverage efficiency. Failure to secure SCADA systems can be catastrophic [1]. For example, a malicious user can take control of the power supply to a city, shut down the water supply system, or cause the malfunction of a nuclear reactor.
Modern SCADA systems have a number of added features which increase the system complexities and are thus difficult to maintain. Some of the added features include control logic, communication protocols, user interfaces, and security. For example, many organizations do not tolerate data delay or data loss. Added features like firewall function and anti-virus software processes can lead to delayed delivery of data [2]. The systems must operate continuously and in tight timing [3]. Moreover, the communications are vulnerable to various threats. In the past few years, the number of cyber-attacks, in general, is rising and has been affecting power station, water, gas, and nuclear control systems. The pattern of cyber-attacks has also evolved beyond the simple attacks such as Denial of Service or Man-in-the-Middle [3].
In December 2015, due to a successful cyber-attack on SCADA, nearly 250,000 people were left without power for hours in Ukraine. After a year, another similar attack hit the country. This attack was launched by using spear phishing emails and is still in practice against industrial organizations. According to the U.S. Department of Justice, there was an attack on a small dam in Rye Brook, New York in 2013. The hackers gained access to the core command-and-control system by using a cellular modem. Although the breach occurred in 2013, it remained unreported until 2016. Furthermore, according to a FBI and Homeland Security joint report [4], there have been cyber-attacks on nuclear power plants throughout the U.S., in which the control systems were targeted. The main motive and severity of the attacks are not known, but the method used for the attack was spear phishing.
SCADA networks also comprise of resource-constrained devices such as Remote Terminal Units and Programming Logic Units, and these devices require lightweight ciphers. Traditional intrusion detection systems (IDSs) are now unable to protect from new threats [5]. Robust security schemes involving machine learning to detect intrusions and encryption algorithms are essential to ensure a secure encrypted communication between nodes in SCADA networks. These threats and attacks have motivated researchers and organizations to develop new robust and secure techniques for SCADA networks.
Although there are several survey papers on security threats, key management schemes, and intrusion detection systems in SCADA networks [6]–[8], the reviews do not provide a comprehensive comparison of the various schemes. The work by Sajid et al. [9] is an excellent survey on the security and challenges of the SCADA systems. However, the paper does not provide a comparison of all the security protocols and standards for SCADA systems. Motivated by this, our paper is an extension of the survey provided by Sajid et al. [9]. It gives a review of the SCADA communication structure and the recent threats faced by them. It then provides a classification and comparative study of the existing security protocols used and proposed to date. Based on the analysis, it also provides the limitations of each of the standards and protocols.
A. Contribution of the Survey
The main contribution in this survey is to provide researchers and organizations with a report that discusses and analyzes the schemes and efforts proposed to secure the SCADA networks. It also gives a comparative study of the existing standards and schemes. Furthermore, it identifies a new threat based on quantum computing faced by SCADA networks.
B. Organization of the Survey
Section II and Section III describe the SCADA communication structure and threats faced by such systems. Section IV describes the attacks on SCADA networks. Section V discusses the threat posed by quantum computing. Section VI gives a thorough study of on-going SCADA security schemes. Section VII discusses the primary factors used for comparison of all the schemes. Section VIII gives a critical analysis of the schemes used to secure the SCADA networks, and Section IX provides concluding remarks.
SCADA Communication Architecture
SCADA systems consist of several entities organized in a hierarchical structure [5]. They are used in monitoring various kinds of infrastructure and industries. They comprise the integration of data acquisition systems, data transmission systems and Human-Machine Interface (HMI) [5]. The HMI is a user interface that connects a person to a device. It is mainly used to visualize data, and monitor production time, machine inputs and outputs. Figure 1 illustrates a generic SCADA network communication architecture [10]–[12]. The HMI is a software interface while the hardware components are as follows [11], [12].
-
Master Station Unit or Master Terminal Unit (MSU/ MTU) is the control center of a SCADA network.
-
Sub-MSU or Sub-MTU acts as a sub-control center. However, it is not needed in some cases. The MSU can connect to the remote station units directly.
-
Remote Station Units are Remote Terminal Unit (RTU), Intelligent End Device (IED) and Programmable Logic Controller (PLC). They are used to monitor sensors and actuators to collect data values.
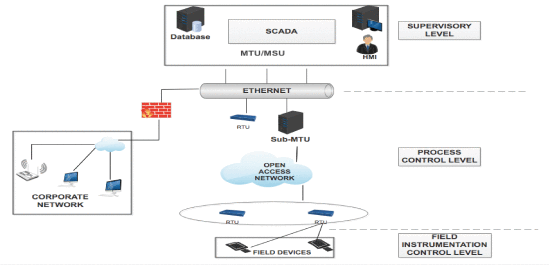
SCADA system architectures have four typical architectural styles [13]:
-
Monolithic: In 1970s, control units or MTUs were hardwired to RTUs.
-
Distributed: In 1980s to 1990s, MTUs and RTUs communicated using communication protocols and servers. However, they did not allow Internet connection.
-
Networked: In 2000s, SCADA architecture started using external networks like the Internet.
-
Web-based SCADA: Currently, users can access SCADA systems using web browsers and mobile devices.
-
Addition of new components such as computers, operating stations, communication servers and other types of resources.
-
Increase in amount of data exchange between units with increase in the number of components.
-
Increase in the amount of interactions between system components.
-
Usage of firewalls and antivirus software that consequently slows down the processing power of the system and leads to delay in data transfer to other units.
Security Threats Faced by SCADA Networks
Like any other system or network, a SCADA network faces the following threats [1], [12].
-
Loss of availability can cause power outages and can have a negative impact on the efficiency of power supply. This condition may have a cascading effect in the physical domain. Thus, achieving availability as a security goal should be one of the primary objectives of a SCADA network.
-
Loss of integrity is a scenario when the attacker modifies the data, and thus, the receiver receives the changed data. This type of scenario is achievable by launching a Man-in-the-Middle attack, which can further result in malware injection and IP spoofing.
-
Loss of confidentiality can be achieved by eavesdropping on a channel. It leads to the loss of privacy and stealing of data as private data is exposed.
-
Repudiation is where the sender denies they have sent the data at that time.
-
Slowloris, GoldenEye for operating system Kali Linux.
-
Lack of authentication in the Distributed Network Protocol 3.0 (DNP 3) used in SCADA systems which can lead to an impersonation attack [14].
Attacks on SCADA Networks
The usage of Internet connectivity, cloud computing, wireless communications, and social engineering on SCADA networks have made its architecture vulnerable [1]. One of the main reasons for the vulnerabilities in SCADA is the lack of strong encryption and real-time monitoring.
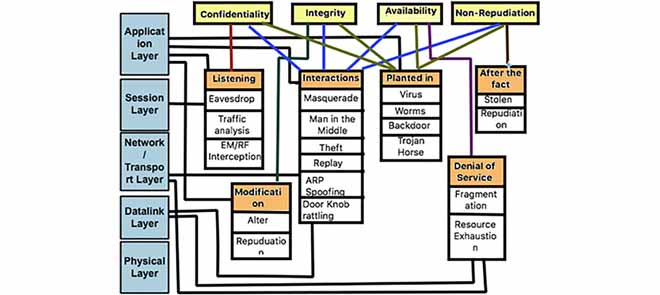
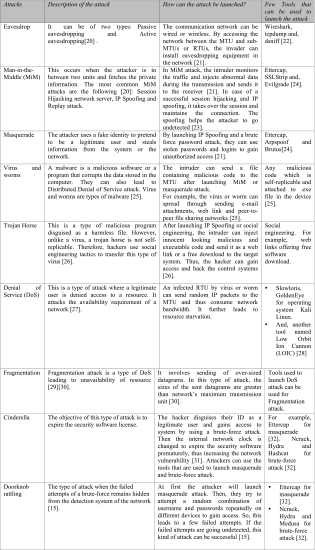
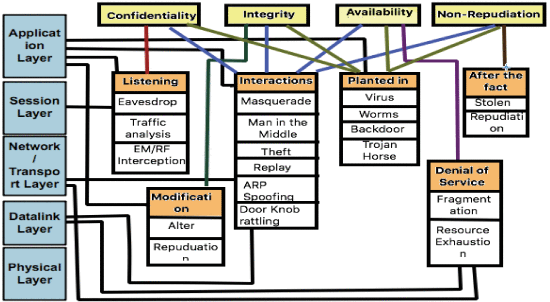
Attacks can occur at all layers from the supervisory level to the field instrumentation level [15]. The most common attacks are outlined in Table 1A and 1B [15]–[19].
They can also be categorized based on attacks on hardware, software, and network connection [15].
-
Attack on hardware: This is a scenario where the hacker gets unauthenticated access to the units and tampers with them or their functions. The primary challenge in securing hardware is access control. For example, the doorknob-rattling attack [15] as explained in Table 1.
-
Attack on software: The SCADA system utilizes a variety of software to enhance its efficiency by fulfilling the functional demands. However, due to poor implementation, it is vulnerable to SQL injection, trojan horse and buffer overflow. These are a few examples of attack on software [15].
-
Attack on network connection: The attack on communication stack can be on the network layer, transport layer, and the application layer. Figure 2 gives a classification of attacks based on the layers of the Open Systems Interconnection (OSI) model and maps them to the violation of security goals, namely, confidentiality, integrity, availability, and non-repudiation [15].
Possible Attack Using Quantum Computing
A. Quantum Computer
Traditional computers are the digital electronic computers which encode information in bits, where each bit can be 0 or 1. They execute algorithms on bits using simple digital logic operations such as AND, OR, and NOT [33]. Instead, quantum computers encode information in qubits which are generated using atoms as digital bits [34]. The value of qubits is based on the rules of modern physics: superposition and entanglement principle. According to the superposition principle, each qubit can represent 0 or 1 or both at the same time. Entanglement occurs when two superposed qubits are allied with each other [34], [35]. Therefore, the number of qubits is directly proportional to the number of states held by the set of qubits [35], [36]. These two principles make quantum computing way faster than traditional computing.
A quantum algorithm was proposed to solve a binary maze problem [37]. Each line has one input and two outputs. The quantum algorithm attempted all the paths at the same time, and therefore, it solved the problem at extreme speed. Whereas, solving the maze problem was hard for a traditional computer since the size of the problem was doubling each time. For example, a 1000 step binary maze has 21000 outcomes, and this took more time in the case of traditional approach [37].
D-wave, a quantum computing company, launched its first commercial quantum computer named D-Wave One in 2011, which is being used by National Aeronautics and Space Administration (NASA) for in-depth space exploration. By 2013, they increased the number of qubits and released the D-Wave Two system. Google is also planning to use a quantum computer for big data mining [35].
B. Brute Force Attack by Using a Quantum Computer
The capacity and speed of quantum computer for solving mathematical problems make them a threat to traditional security schemes. All the encryption schemes are derived from mathematical logic. Cracking these schemes may be possible for quantum computers [38], [39]. One such problem is Elliptic curve cryptography (ECC or ECDSA). Using Shor’s algorithm, a quantum computer can launch a brute force attack and crack ECC in a brief time [39].
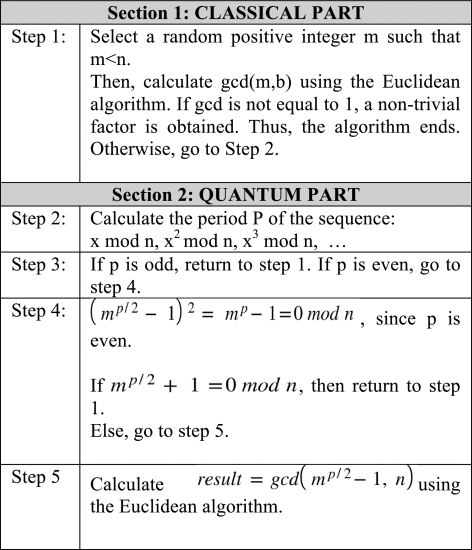
Shor’s algorithm is a quantum algorithm for factorizing a number [40]. It implies that any public key cryptography can be easily cracked. The algorithm has two sections as follows [41]. Table 2 shows the steps.
-
The classical computer can compute Section 1 in Table 2. It reduces the factoring problem to an order finding problem using the Euclidean algorithm. The Euclidean algorithm is a fast scheme to calculate the greatest common divisor (gcd) of two integers [42].
-
Section 2 is the quantum part which used order finding algorithm. It finds the period of the function using the Quantum Fourier Transform (QFT).
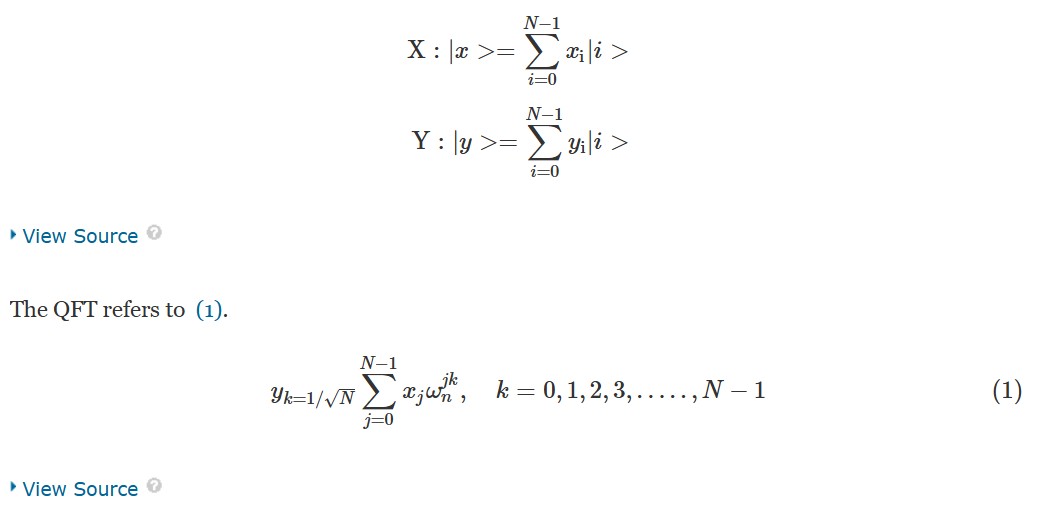
Existing security standards and schemes are based on traditional cryptography such as Advanced Encryption System (AES), Elliptic-curve cryptography (ECC), and Secure Hash Algorithm (SHA). Therefore, they are vulnerable to quantum attacks. The transformation of quantum computing from theory to practice in the recent past has not only brought with its potential advantages but also increasing threats [38], [39].
Existing SCADA Security Schemes
An attack on a SCADA system may have many adverse effects. Due to this reason, organizations and researchers have been putting much effort into developing standards, protocols, and security schemes. The existing security schemes can be categorized based on: current standards, detection of SCADA attacks, and prevention of SCADA attacks.
Classification 1: Current standards can be divided into two categories: Standard Providing Guidelines and Standards acting as crypto-suites. These standards are used in practice depending on the particular industry’s requirements. However, the mechanisms of thwarting attacks in the standards are either not clearly discussed or, are not strongly secure.
Thus, to add more security in the existing standards for SCADA, many researchers have proposed novel schemes. In this paper, the academic effort has been further classified into two following categories:
Classification 2: Detection of SCADA attacks consists of all the proposed intrusion detection systems for SCADA networks. The main objective is to overcome the lack of availability that is one of the security requirements.
Classification 3: Prevention of SCADA attacks consists of all the key management protocols proposed to secure the communication between the units.
A. Current Standards
Throughout the world, over 10 countries have proposed more than 40 standards and protocols. The available standards are described as follows [44], [45]. Few of the standards provide guidelines to secure an infrastructure from physical and cyber-attacks. Furthermore, the remaining standards include a major part that acts as a crypto-suite. In this paper, they are categorized into two: 1) Security guidelines-based Standards and 2) Crypto-suites based Standards.
1) Security Guidelines Based Standards
a: IEEE 1402
Institute of Electrical and Electronics Engineers (IEEE) 1402–2000 is an IEEE Guide for Electric Power Substation Physical and Electronic Security. The Power Engineering Society/Substations of IEEE sponsors the standard. It discusses security issues caused by human intrusion at power supply substations along with methods and schemes to mitigate physical and electronic intrusions [46].
In the guide, the intrusions are classified into four main categories: pedestrian, vehicular, projectile, and electronic intrusion [45], [46]. The paper also categorizes the security methods used at power control substations [45], [46].
The computer security systems include using passwords, dial-back verification, selective access, virus scans, and encryption. The guide also explains the substation security plan and categorizes it into three questions: Why is the plan required? Who may monitor the plan? What security methods are needed? According to the guide, these are the main criteria on which the security plan should be executed [45], [46].
IEEE 1402 does not solely focus on the information security. Rather, it gives a broad and general guideline for physical as well as cyber security.
b: ISO 17799 – “Information Technology – Code of Practice for Information Security Management”
The International Organization for Standardization (ISO) published ISO 17799 in December 2000. The ISO 17799 is an international guideline for monitoring information security management of any organization [45]. The standard refers to information as an asset that is valuable to industry. The main objective of the standard is to protect the asset by preserving confidentiality, integrity and availability [47].
ISO 17799 provides a structured guideline to control security and perform security risk assessment. It provides the following benefits [47].
-
Organizational Security
-
Asset Classification
-
Personnel security
-
Physical and environmental security
-
Network management that involves media handling, backup schedules and logging.
-
Access control
-
Maintenance of cryptographic controls and system integrity.
c: ISO 15408 – “Common Criteria for Information Technology Security Evaluation”
ISO developed the “Common Criteria got Information Technology Security Evaluation” in January 2004 [45]. The criteria are used to evaluate various functional classes as listed as follows [48].
-
Audit
-
Communication
-
Cryptographic support
-
User data protection
-
Identification and authentication
-
Security Management
-
Privacy
-
Security functions protection
-
Resource Utilization
-
Access
-
Trusted path/channels
However, the report does not focus on the utilization of cryptographic designs in communication and control applications [45]. Furthermore, it does not uniquely focus on the need of physical security in SCADA structure.
d: NERC Security Guidelines – “Security Guidelines for the Electricity Sector: Physical Security”
On June 14, 2002, North American Electric Reliability Council (NERC) releases a version 1.0 of NERC Security Guidelines discusses physical and cyber security along with the general practices for protecting the power supply infrastructure systems [45].
The general guideline focuses on the need of the physical security to maintain the integrity and availability of electric power systems, for example, promoting and deploying the security standards and procedures, periodic evaluation of the security measures, monitoring and reporting threats to the operating section, and quick recovery of the delivery services if damaged [49].
The report also guides to follow a strategy ‘Protection in Depth’. The objective of this strategy is to delay the progress of an attacker. This buys time to the organization to defend and recover against the attack [49].
However, the security guidelines focus mainly on physical security. In 2003, NERC produced a report that deals with cyber security parameters.
e: NERC 1200 – “Urgent Action Standard 1200 – Cyber Security” and NERC 1300 – “Cyber Security”
NERC developed a temporary standard named “Urgent Action Standard 1200” for setting a set of security requirements for the energy industry infrastructure. NERC adopted this standard on August 13th, 2003 for a one-year period and later, it extended the standard till August 2006 [45].
NERC developed NERC 1300 to replace NERC 1200 by addressing the security requirements and recommendations mentioned in NERC 1200 [45], [50]. NERC 1300 focuses on both physical and cyber security. The report has a section that implies that a responsible industry should follow the System Security Management to prevent any malicious cyber activity. The Management section mainly involves the following security measures [50]:
-
Account and Strong Password management.
-
Using security patch manager to check security updates.
-
Using anti-virus monthly.
-
Performing vulnerability assessment at least annually.
-
Preserving and auditing system logs quarterly.
-
Using operating status monitoring tools.
-
Back-up of information on computer systems.
-
Disabling unused ports.
f: API 1164 – “SCADA Security”
API 1164 has three editions. The first edition was released in September 2004. It specifies guidance to secure the SCADA system used in the oil and pipeline infrastructures [45], [51]. It addresses the following issues mentioned in Table 3 [45].
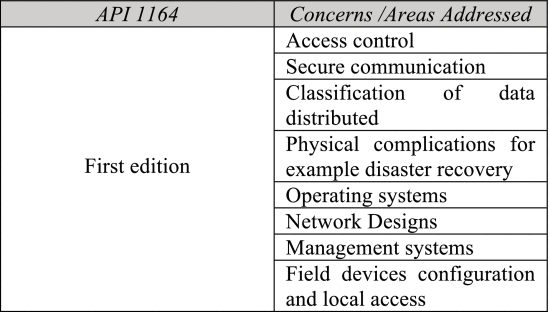
The second edition is the API – “Security Guidance for the Petroleum Industry.” Oil and gas infrastructures utilize this standard to prevent terrorist attacks [45].
The American Petroleum Institute and the National Petrochemical and Refiners Association mutually developed the third edition named API- “Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries”. It is utilized for evaluating various kinds of threats, vulnerabilities, and aftereffects of terrorist attacks [45].
The above-discussed standards are general guidelines to protect the infrastructure of an organization. They do not involve any in-depth discussion of cryptographic algorithms or any technical methodology to detect or protect from any attack. However, the following standards use crypto-suites.
2) Crypto-Suite Standards
a: IEC 62210 – “Data and Communication Security”
In 1999, IEC 62210 was developed by the International Electrotechnical Commission (IEC) as the report of IEC TC 57 AHWG06. Later, AHGW06 was systemized into Working Group (WG) 15 upon Data and Communications Security. Later, it was published in 2003. The IEC TC57 WG15 developed the cybersecurity standards for power control system communications [45].
The working group report describes the security process for the power control systems which involves the corporate security policy, network security protocol, and the end to end application security. The security scheme was also utilized for encrypting communication in the network [45].
AHWG06 issued the report recommending establishing the following tasks [45]:
-
Consequence analysis combined with ISO 15408
-
Attention to the application layer
-
Address key management
-
Address end-to-end security
b: IEC 62351 – “Data and Communication Security”
International Electrotechnical Commission (IEC) developed IEC 62351 to address the deficiency in IEC 62210. The standard is classified into as shown in Table 4 [45], [52]:
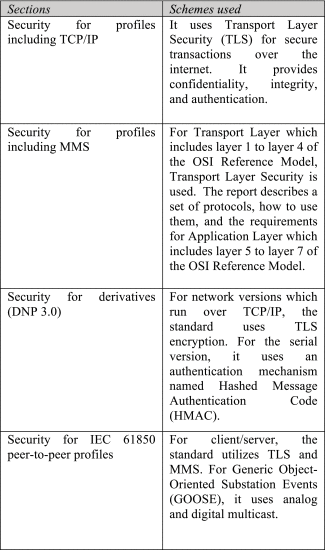
Using TLS security, IEC 62351 provides defense mechanisms against various attacks including spoofing, message replay attack and to some extent Denial-of-Service (DoS) attacks. However, it involves simple encryption schemes.
Immediately after the 9/11 attack, the American Gas Association (AGA) decided to improve the security mechanism which can protect SCADA communication from malicious users. The primary purpose of the standard was to develop a security scheme which can provide security as well as save time and computation cost [44].
c: AGA-12 – “Cryptographic Protection for SCADA Communications General Recommendations”
Traditional security protocols used in SCADA systems such as IEC 60870, DNP3, IEC 61850 and Modbus lack proper security services [14]. However, the new protocol AGA-12 provides security features to the SCADA systems. It uses cryptographic suites to secure the wireless communication between field devices and the MTUs [14], [45]. The steps in AGA-12 is described in Table 5 [44].